In order to close these gaps, every CISO needs the right set of skills, tools, resources, and insights to help guide and gain clarity on focusing on the end goal of getting to a more optimized maturity level.
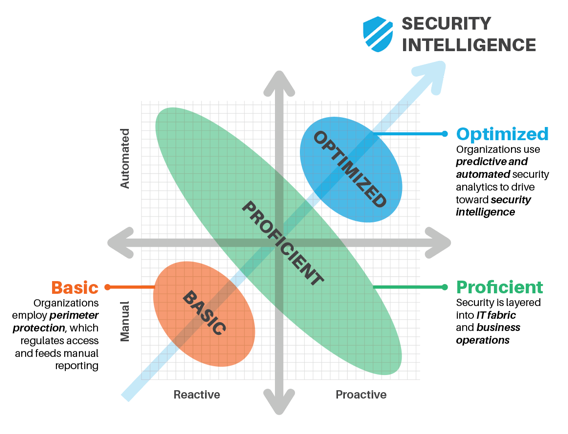

At the Optimized level, you will begin activating artificial intelligence (AI) to help you gain efficiency and intelligence in your security processes. This level includes:
- Integrating a digital forensics and incident response platform into your environment.
- Employing user behavior analytics to identify patterns and at-risk user behaviors.
- Performing automatic data discovery and classification to determine access levels.
- Deploying an intelligent unified endpoint management (UEM) tool that incorporates IoT analytics for both endpoints and mobile devices.
- Managing your encryption keys for both cloud and on-premise data encryption.
- Deploying continuous vulnerability testing for your applications.
- Leveraging external threat intelligence services to keep up to date.
- Using analytics software to do predictive event analytics.
At the Proficient level, you need to begin automating some of your security processes to reduce human intervention. This level includes:
- Integrating a centralized event management tool for all of your systems, servers and network devices.
- Deploying a centralized malware protection platform across all of your endpoints.
- Protecting all of your business systems against data loss by using DLP technology.
- Using a data masking tool to protect your sensitive business information.
- Monitoring your data and file access in real-time.
- Configuring a Single Sign On (SSO) platform to manage Web access.
- Activating multi-factor authentication on your business applications.
- Periodically scanning for vulnerabilities.
At the Basic level, you need to begin using digital compliance tools. The purpose is to establish a foundation that you can use to build your compliance intelligence. This level includes:
- Integrating a centralized log management tool to collect information from all of your systems, servers and network devices.
- Deploying a centralized anti-virus and patch management platform across all of your endpoints.
- Defining a centralized user directory to handle access and permissions for all of your users.
- Encrypting the sensitive data residing on your servers.

At the Optimized level, you will begin activating artificial intelligence (AI) to help you gain efficiency and intelligence in your security processes. This level will include:
- Integrating a digital forensics and incident response investigation tool into your environment.
- Employing user behavior analytics to identify patterns and at-risk user behaviors.
- Deploying an intelligent unified endpoint management (UEM) tool that incorporates IoT analytics for both endpoints and mobile devices.
- Leveraging external threat intelligence services to keep up to date.
- Using analytics software to do predictive event analytics.
- Deploying security procedures and a platform for threat hunting and investigation.
- Automating incident response.
At the Proficient level, you need to begin automating some of your security processes to reduce human intervention. This level will include:
- Integrating a centralized event management tool for all your systems, servers and network devices.
- Deploying a centralized malware protection platform across all of your endpoints.
- Protecting all of your business systems against data loss by using DLP technology.
- Using a data masking tool to protect your sensitive business information.
- Monitoring your data and file access in real-time.
- Configuring a Single Sign On (SSO) platform to manage Web access.
- Deploying a centralized identity management platform for all of your systems.
At the Basic level, you need to protect your organization against threats. The purpose is to establish the foundation that you can use to build your threat protection intelligence. This level includes:
- Integrating a centralized log management tool to collect information from all of your systems, servers and network devices.
- Deploying a centralized anti-virus and patch management platform across all of your endpoints.
- Defining a centralized user directory to handle access and permissions for all of your users.
- Enforcing a security policy of “less privileges”.

At the Optimized level, you will begin activating artificial intelligence (AI) to help you gain efficiency and intelligence in your security processes. This level will include:
- Employing user behavior analytics to identify patterns and at-risk user behaviors.
- Integrating a digital forensics and incident response investigation tool into your environment.
- Using analytics software to do predictive event analytics.
- Deploying an intelligent unified endpoint management (UEM) tool that incorporates IoT analytics for both endpoints and mobile devices.
- Deploying continuous vulnerability testing for your applications.
- Performing automatic data discovery and classification to determine access levels.
- Managing your encryption keys for both cloud and on-premise data encryption.
- Integrating omni-channel fraud detection.
At the Proficient level, you need to begin automating some of your security processes to reduce human intervention. This level includes:
- Activating multi-factor authentication on your business applications.
- Configuring a Single Sign On (SSO) platform to manage all of your Web accesses.
- Integrating a centralized event management tool for all your systems, servers and network devices.
- Protecting all of your business systems against data loss by using DLP technology.
- Periodically scanning for vulnerabilities.
- Monitoring your data and file access in real-time.
- Using a data masking tool to protect your sensitive business information.
- Deploying a centralized malware protection platform across all of your endpoints.
- Deploying an advanced enterprise mobility management (EMM) and mobile device management (MDM) tool to handle application control and application content monitoring.
At the Basic level, you need to build the foundation so your enterprise can digitally transform in a secure way. This level includes:
- Defining a centralized user directory to handle access and permissions for all of your users.
- Enforcing a security policy of “less privileges”.
- Integrating a centralized log management tool to collect information from all of your systems, servers and network devices.
- Deploying a centralized anti-virus and patch management platform across all of your endpoints.
- Encrypting the sensitive data residing on your servers.
Deploy a pilot project in 3 months or less and let us manage the cloud-based solution for you!
To start your journey today, it all starts at the innovation garage, book a visit to our innovation garage today!



